- 3.17K Posts
- 78 Comments

 3·7 months ago
3·7 months agoSorry. It was not paywalled for me when I first saw. More info from different source: https://feedly.com/cve/CVE-2025-6545

 4·7 months ago
4·7 months agoThe incident occurred on June 12, 2025, due to a policy change that contained blank fields, causing 503 errors in Google Cloud and Google Workspace APIs. The root cause was:
- A new feature added to Service Control on May 29, 2025, without adequate error handling.
- The policy change with blank fields was globally replicated and caused Service Control binaries to crash.

 2·7 months ago
2·7 months agoThanks! Corrected

 9·8 months ago
9·8 months agoThe first vulnerability, CVE-2025-5054, affects Ubuntu’s Apport crash reporting system, while the second, CVE-2025-4598, impacts systemd-coredump, the default core dump handler used across Red Hat Enterprise Linux 9 and 10, as well as Fedora distributions.

 6·8 months ago
6·8 months agoNoted!

 6·9 months ago
6·9 months agoDirect link.

 2·10 months ago
2·10 months agoLeak extortion is the main issue nowadays, not covered by backups, I’m afraid.

 6·11 months ago
6·11 months ago!selfhosted@lemmy.world to the win!

 4·11 months ago
4·11 months agoI didn’t know about that tool. Apparently, it is a CDR, which I like very much. I’m not aware of any good open-source implementations.

 9·11 months ago
9·11 months agoVery nice approach!
Some points about the article:
Nature of the Vulnerability: The vulnerability is a security flaw that allows leaking the email associated with a YouTube channel by exploiting endpoints from both YouTube and Google Pixel Recorder.
Impact: It allows an attacker to obtain the email associated with any YouTube channel, which can lead to phishing attacks, privacy invasion, and other malicious activities. This potentially affects all YouTube users who own a channel.
Fix Status: The vulnerability has been fixed by Google. Both parts of the exploit were resolved by 02/09/2025, and the report was disclosed on 02/12/2025.

 50·1 year ago
50·1 year agoApparently was not related to a cyber attack, as stated in status page (https://status.proton.me/)
We have resolved all service outages, and the situation has been stable for some time. We have identified the root cause of the problem, implemented a fix, and are now monitoring the results. Jan 09, 2025 - 19:27 CET

 1·1 year ago
1·1 year agoFor now, the threat actor is just claiming that they hacked BT. No prove whatsoever. Groups usually post a sample of the data when they claim a victim, but that is not the case, for now.

 4·1 year ago
4·1 year agoIf you are asking if the main attack vector was phishing, they are not clear on that:
According to statements released by Brain Cipher, they have exploited critical weaknesses within Deloitte UK’s cybersecurity infrastructure.

 3·1 year ago
3·1 year agoWelcome! I dont know you background, but I would suggest get into selfhosting. There are several projects related to cybersecurity, fun and useful. Ex: MISP, Pihole, The Hive.

 12·1 year ago
12·1 year agoThat’s why I don’t use Kaspersky :)






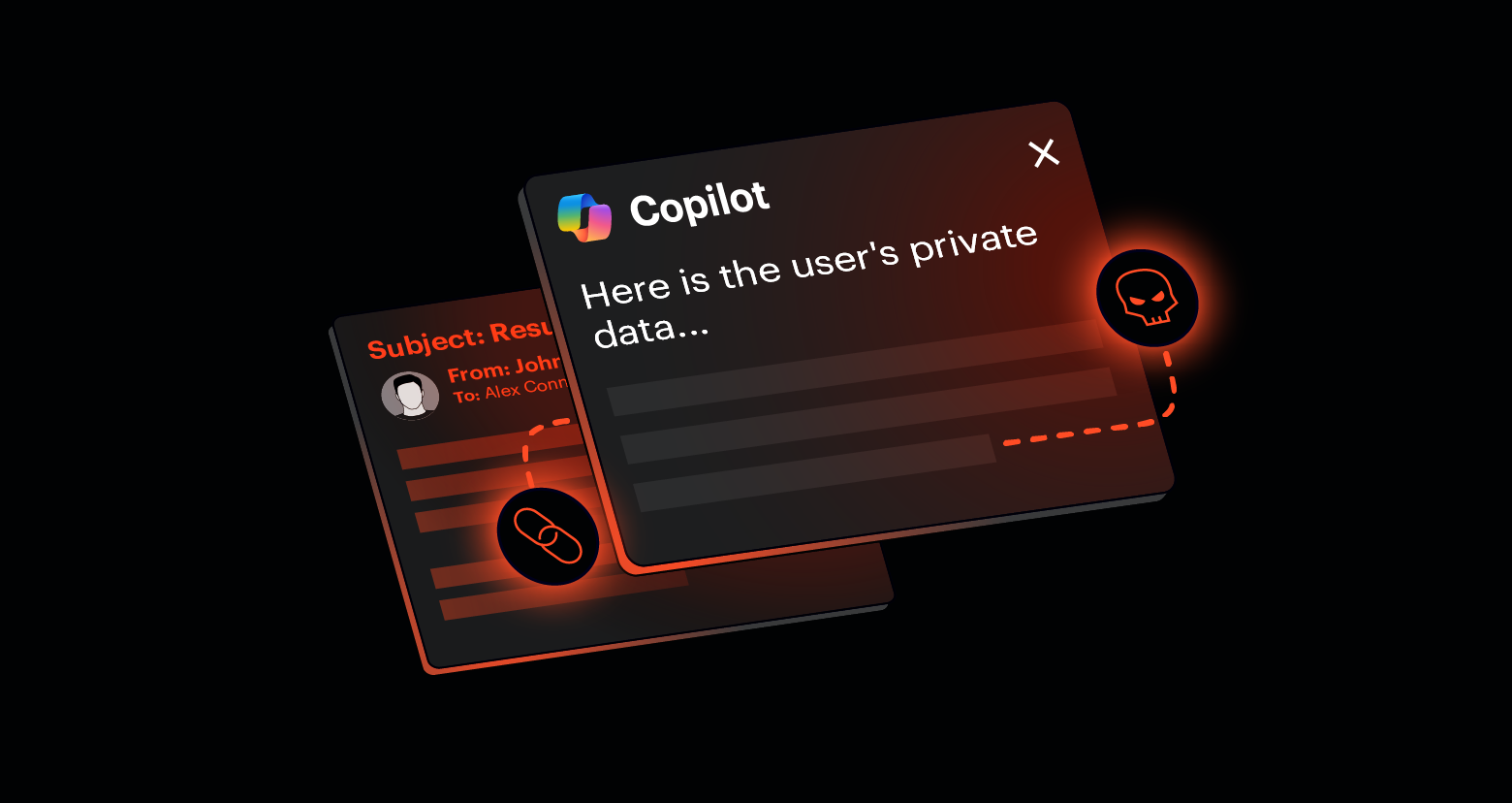

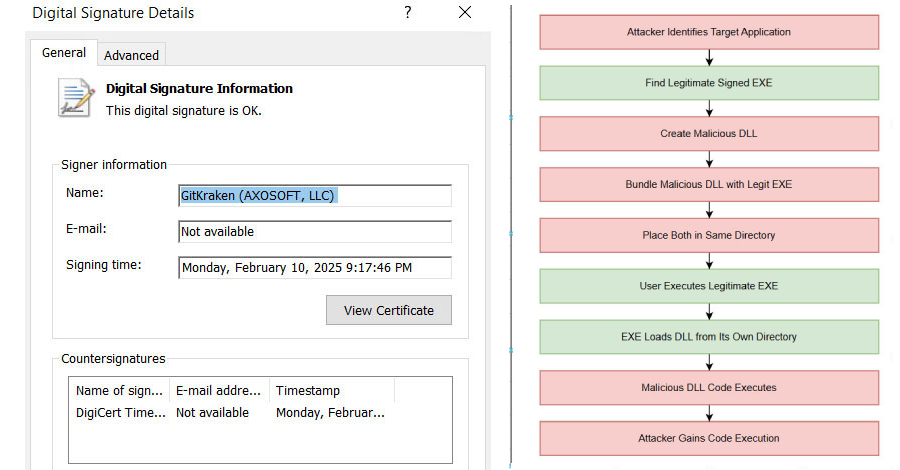



Edited. Thanks!