English
English- •
- www.bitdefender.com
- •
- 1d
- •
> A Korean cybersecurity expert has been sentenced to prison for illegally
> accessing and distributing private videos from vulnerable "wallpad" cameras in
> 400,000 private households.
 English
English- •
- www.bleepingcomputer.com
- •
- 2h
- •
> Microsoft has fixed a zero-day vulnerability exploited in attacks to deliver QakBot and other malware payloads on vulnerable Windows systems.
 English
English- •
- krebsonsecurity.com
- •
- 19h
- •
> Last week, the United States joined the U.K. and Australia in sanctioning and charging a Russian man named Dmitry Yuryevich Khoroshev as the leader of the infamous LockBit ransomware group. LockBit’s leader “LockBitSupp” claims the feds named the wrong guy, saying the charges don’t explain how they connected him to Khoroshev. This post examines the activities of Khoroshev’s many alter egos on the cybercrime forums, and tracks the career of a gifted malware author who has written and sold malicious code for the past 14 years.
 English
English- •
- www.bleepingcomputer.com
- •
- 1d
- •
> Threat actors are using Domain Name System (DNS) tunneling to track when their targets open phishing emails and click on malicious links, and to scan networks for potential vulnerabilities.
 English
English- •
- www.bleepingcomputer.com
- •
- 1d
- •
> A new package mimicked the popular 'requests' library on the Python Package Index (PyPI) to target macOS devices with the Sliver C2 adversary framework, used for gaining initial access to corporate networks.
 English
English- •
- www.bleepingcomputer.com
- •
- 1d
- •
> Apple has backported security patches released in March to older iPhones and iPads, fixing an iOS Kernel zero-day tagged as exploited in attacks.
 English
English- •
- www.bleepingcomputer.com
- •
- 1d
- •
> Since April, millions of phishing emails have been sent through the Phorpiex botnet to conduct a large-scale LockBit Black ransomware campaign.
- Kid English
- •
- breachforums.st
- •
- 4d
- •
Data offered include Alliance employees, FOUO source code, PDFs, Documents for recon and guidelines.
- @runswithjedi@lemmy.world English
- •
- 6d
- •
I contacted Proton VPN about the TunnelVision exploit and I got a response. I feel great about it, thank you Proton!
>Hi,
>
>
>Thank you for your patience.
>
>
>Our engineers have conducted a thorough analysis of this threat, reconstructed it experimentally, and tested it on Proton VPN. Please note that the attack can only be carried out if the local network itself is compromised.
>
>
>Regardless, we're working on a fix for our Linux application that will provide full protection against it, and it'll be released as soon as possible.
>
>
>If there's anything else that I can help you with in the meantime, please feel free to let me know.
>
>
>Have a nice day!
 English
English- •
- www.bleepingcomputer.com
- •
- 7d
- •
> BetterHelp has agreed to pay $7.8 million in a settlement agreement with the U.S. Federal Trade Commission (FTC) over allegations of misusing and sharing consumer health data for advertising purposes.
 English
English- •
- arstechnica.com
- •
- 6d
- •
> Hackers can exploit them to gain full administrative control of internal devices.
 English
English- •
- www.csoonline.com
- •
- 7d
- •
> Organizations that eschew cyber insurance give up not only financial protection but also advice from the insurer on improving the security of their systems.
 English
English- •
- www.csoonline.com
- •
- 6d
- •
> Five years after being discovered, the Kinsing cryptojacking operation remains very active against organizations, employing daily probes for vulnerable applications using an ever-growing list of exploits.
- Kid English
- •
- securelist.com
- •
- 7d
- •
Kaspersky's report highlights a steady increase in software vulnerabilities, with a surge in critical ones due to factors like bug bounty programs and complex software. Exploits, especially those available publicly, pose significant threats, and their numbers are rising. Key vulnerabilities in Q1 2024 include those affecting XZ, Visual Studio, runc, ScreenConnect, Windows Defender, and TeamCity.
 English
English- •
- www.buskill.in
- •
- 7d
- •
Today we're ecstatic to [publish our first demo](https://www.buskill.in/3d-print-2024-05/) showing a homemade BusKill Cable (in the prototype 3D-printed case) triggering a lockscreen.
| [](https://www.buskill.in/3d-print-2024-05/) |
|:--:|
| *Watch the [3D-Printed USB Dead Man Switch (Prototype Demo)](https://www.youtube.com/v/vFTQatw94VU) for more info [youtube.com/v/vFTQatw94VU](https://www.youtube.com/v/vFTQatw94VU)* |
via [@Goldfishlaser@lemmy.ml](https://lemmy.ml/u/Goldfishlaser)
In our [last update](https://www.buskill.in/3d-print-2023-08/), I showed a video demo where I successfully triggered a lockscreen using a BusKill prototype without the 3D-printed body for the case and N35 disc magnets. I realized that the N35 disc magnets were not strong enough. In this update, I show a demo with the prototype built inside a 3D-printed case and with (stronger) N42 and N52 cube magnets.
# What is BusKill?
BusKill is a laptop kill-cord. It's a USB cable with a magnetic breakaway that you attach to your body and connect to your computer.
| [](https://www.buskill.in/#demo) |
|:--:|
| *Watch the [BusKill Explainer Video](https://www.buskill.in/#demo) for more info [youtube.com/v/qPwyoD_cQR4](https://www.youtube.com/v/qPwyoD_cQR4)* |
If the connection between you to your computer is severed, then your device will lock, shutdown, or shred its encryption keys -- thus keeping your encrypted data safe from thieves that steal your device.
# Why?
While [we do what we can](https://www.buskill.in//buskill-onion-service-tor/) to allow at-risk folks to [purchase BusKill cables anonymously](https://www.buskill.in//bitcoin-black-friday-2023/#privacy), there is always the risk of [interdiction](https://docs.buskill.in/buskill-app/en/stable/faq.html#q-what-about-interdiction).
We don't consider hologram stickers or tamper-evident tape/crisps/glitter to be sufficient solutions to supply-chain security. Rather, the solution to these attacks is to build open-source, easily inspectable hardware whose integrity can be validated without damaging the device and without sophisticated technology.
Actually, the best way to confirm the integrity of your hardware is to build it yourself. Fortunately, BusKill doesn't have any circuit boards, microcontrollers, or silicon; it's trivial to print your own BusKill cable -- which is essentially a USB extension cable with a magnetic breakaway in the middle
Mitigating interdiction via 3D printing is one of many reasons that [Melanie Allen](https://github.com/Goldfishlaser) has been diligently working on prototyping a 3D-printable BusKill cable this year. In this article, we hope to showcase her progress and provide you with some OpenSCAD and `.stl` files you can use to build your own version of the prototype, if you want to help us test and improve the design.
# Print BusKill
[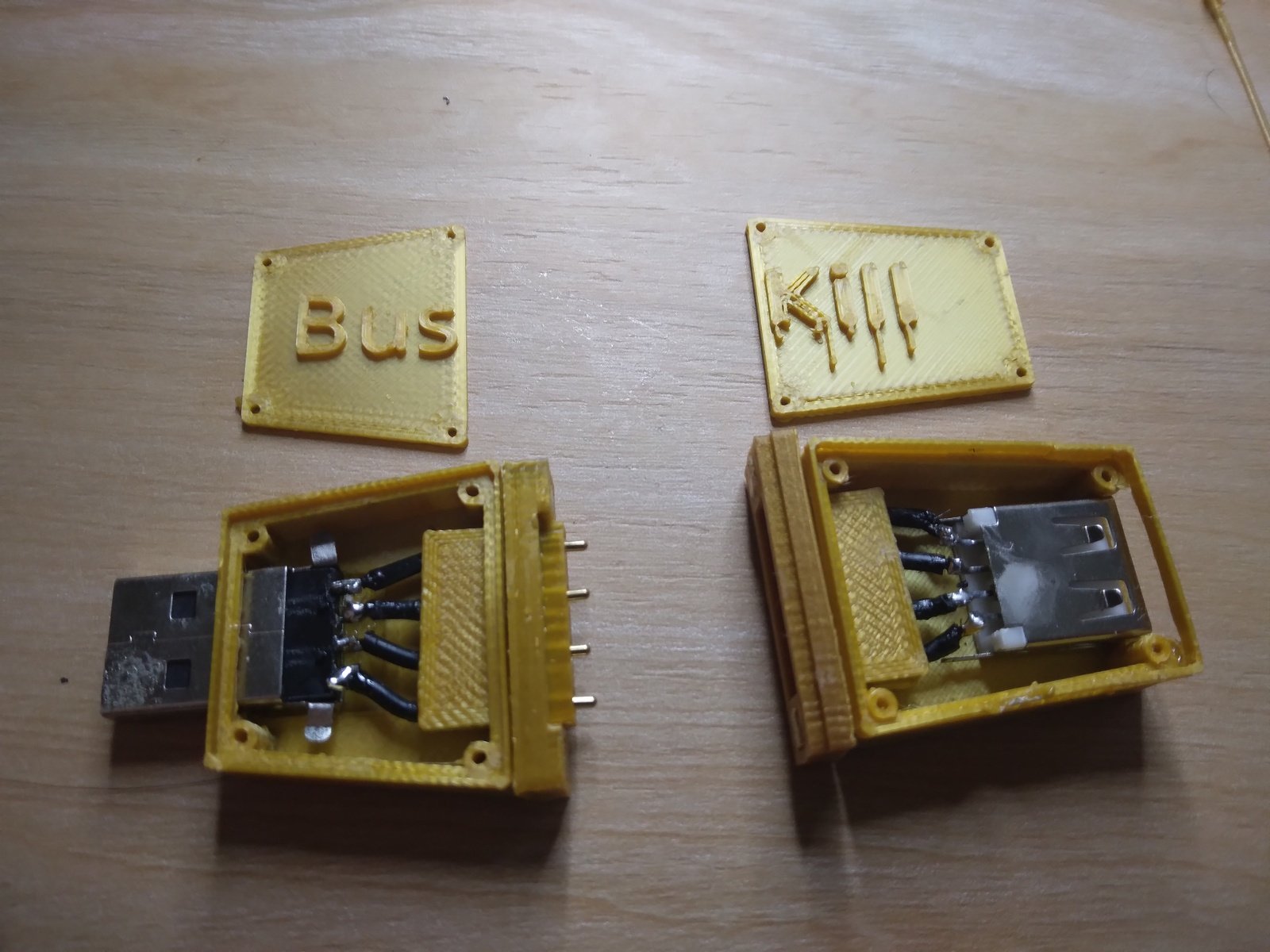](https://www.buskill.in/3d-print-2024-05/)
If you'd like to reproduce our experiment and print your own BusKill cable prototype, you can [download the stl files](https://www.buskill.in/3d-print-2024-05/) and [read our instructions](https://www.buskill.in/3d-print-2024-05/) here:
* [buskill.in/3d-print-2024-05](https://www.buskill.in/3d-print-2024-05/)
# Iterate with us!
**If you have access to a 3D Printer, you have basic EE experience, or you'd like to help us test our 3D printable BusKill prototype, please** [let us know](https://buskill.in/contact). The whole is greater than the sum of its parts, and we're eager to finish-off this 3D printable BusKill prototype to help make this security-critical tool accessible to more people world-wide!
Cybersecurity
!cybersecurity@sh.itjust.worksYou are not logged in. However you can subscribe from another Fediverse account, for example Lemmy or Mastodon. To do this, paste the following into the search field of your instance: !cybersecurity@sh.itjust.works
c/cybersecurity is a community centered on the cybersecurity and information security profession. You can come here to discuss news, post something interesting, or just chat with others.
THE RULES
Instance Rules
- Be respectful. Everyone should feel welcome here.
- No bigotry - including racism, sexism, ableism, homophobia, transphobia, or xenophobia.
- No Ads / Spamming.
- No pornography.
Community Rules
- Idk, keep it semi-professional?
- Nothing illegal. We’re all ethical here.
- Rules will be added/redefined as necessary.
If you ask someone to hack your “friends” socials you’re just going to get banned so don’t do that.
Learn about hacking
Other security-related communities !databreaches@lemmy.zip !netsec@lemmy.world !cybersecurity@lemmy.capebreton.social !securitynews@infosec.pub !netsec@links.hackliberty.org !cybersecurity@infosec.pub !pulse_of_truth@infosec.pub
Notable mention to !cybersecuritymemes@lemmy.world
- 1 user online
- 13 users / day
- 30 users / week
- 132 users / month
- 533 users / 6 months
- 1 subscriber
- 670 Posts
- 1.34K Comments
- Modlog
- mods:
- Kid

sh.itjust.works

A bilingual (EN/FR) general-purpose instance located in eastern Canada! Powered by 99% renewable energy! Everyone is welcome eh.
Useful Links
Rules:
- Be respectful. Everyone should feel welcome here.
- No bigotry - including racism, sexism, ableism, homophobia, transphobia, or xenophobia.
- No Ads / Spamming.
- No pornography.
Règles :
- Soyez respectueux. Tout le monde doit se sentir le bienvenu ici.
- Pas de bigoterie - y compris le racisme, le sexisme, le capacitisme, l’homophobie, la transphobie ou la xénophobie.
- Pas de publicités / Pas de spam.
- Pas de pornographie.
Other UI options (more to come)
Monitoring Services
lemmy-meter.info