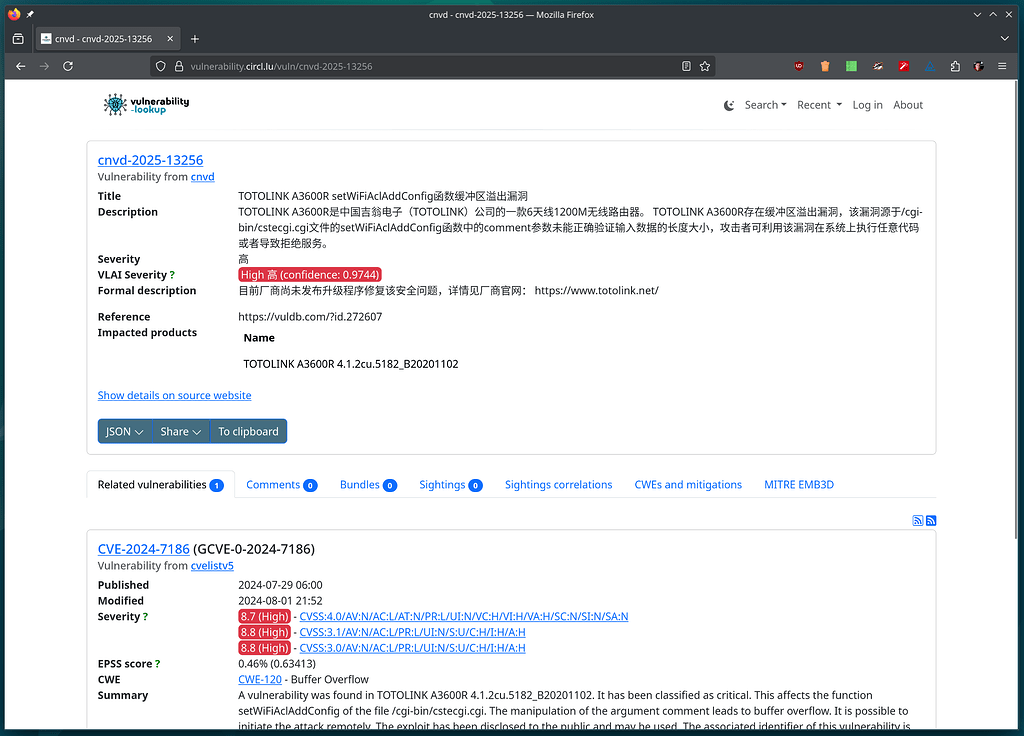
Most of the time, yes. It has a relation with the impact. I’m referring to activity on social networks such as Mastodon and Bluesky, but also to other sources like Nuclei templates, Metasploit modules, and the Shadowserver Honeypot dataset. We rely on different types of sightings. It’s not just about “mentions.” The sightings used in the reports are from different sources: https://www.vulnerability-lookup.org/tools/#sightings
Regarding social network mentions, especially on platforms like Bluesky, I was quite skeptical at first since there’s a lot of noise. Lot of people are simply ranting. I changed my mind on this. Honestly, most of the time when we observe a spike in activity shortly after — or even before — the publication of an advisory, it turns out to be a severe vulnerability. Or something we have to look at.
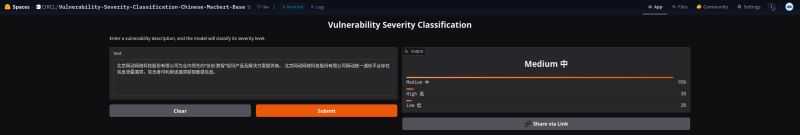
We discussed this topic in our paper presented in Berlin: https://www.vulnerability-lookup.org/events/#first-cyber-threat-intelligence-conference , and more recently, we explored its connection with forecasting and automated classification techniques in our paper “VLAI: A RoBERTa-Based Model for Automated Vulnerability Severity Classification.”


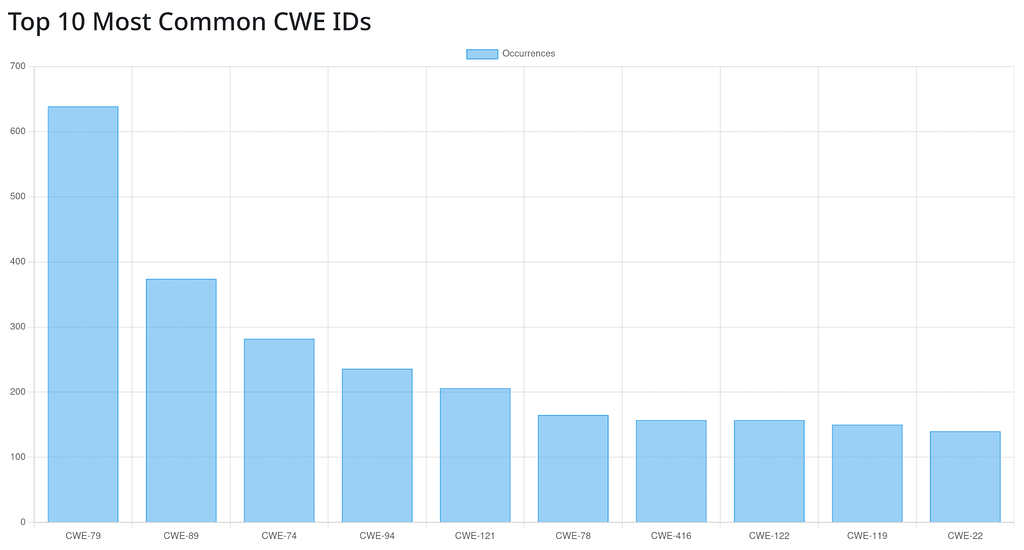
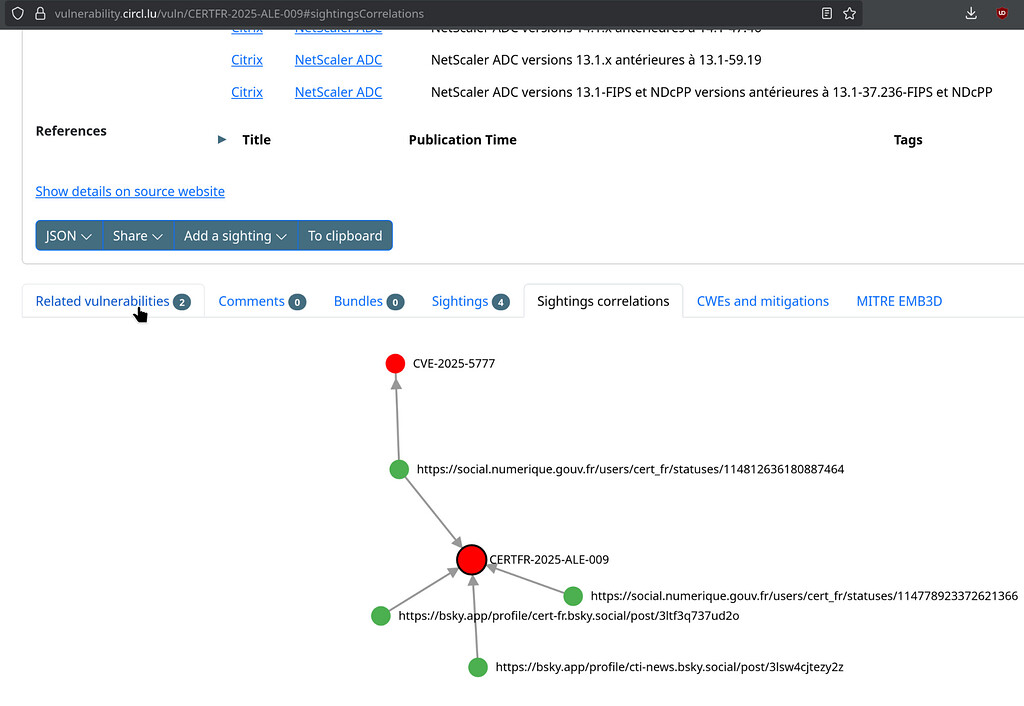
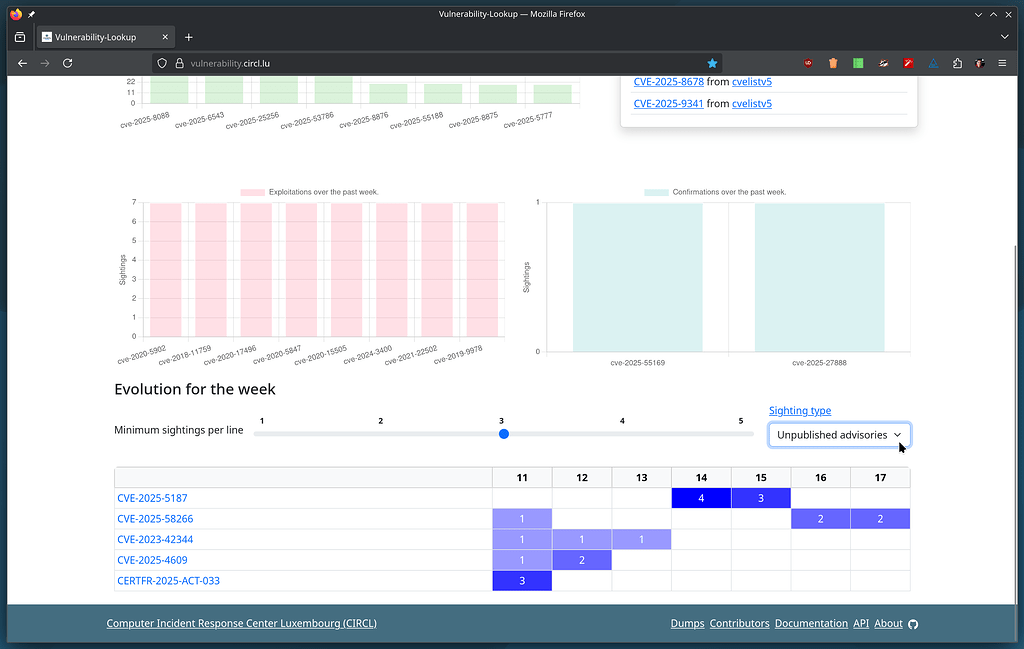
Considering vendor ranking. I see this quite often. Recently during Vuln4Cast conference. I think we will try some CNA ranking as well. Just to see. Or make a CNA classification. For example some CNAs often publish advisories related to Wordpress vulnerabilities that are barely maintained. I would like to be able to make stats including or excluding various CNAs, vendors, etc. We need first to handle couple of new indexes in our system for this.